Due to factors such as the low threshold of game cheating, unequal game security confrontation, the perfect development of the black and gray industry chain, and the high threshold of legal rights, the situation of game security is getting more and more serious, and “game anti-cheat” has become a mandatory course for vendors.
Based on more than ten years of game security confrontation experience, JikGuard will analyze and share with you the principles and classifications of game cheats implementation and the dimensions of game anti-cheat solutions, combined with case studies.

Common game cheats attacks include: injection, memory modification, speed hack, auto-click, packet capture, virtual environment, hack and so on.
Injection Cheats Case Study
Injection cheats, as the name suggests, is to inject the cheat module into the game process space, and at the same time, execute the entry function of the functional module, which mostly involves memory operation and rich functionality.From the injection process, Android system generally adopts SO injection, ptrace injection, Zygote injection and infected ELF files. iOS system can be realized by injecting dylib using Cydia framework after jailbreak.
After opening the cheats and successfully injecting into the game, the cheats interface guides the player to use the function, and then call the interface function to hook the corresponding function with HOOK operation, rewrite the parameters, or call the logic, so as to realize the function of the cheats.

Hook for Android
Compared with other types of cheats, the way of modifying game code logic is more flexible and diversified, and the hackers will hide the injected module by various means, which makes the investigation of the injected cheats more difficult and longer, and the negative impact on the game is also more serious.
Memory modification cheats case study
Memory modification cheats are the most common type of cheats. The principle of implementation is to search and locate the game memory through memory modifiers, and then modify the numerical modules.For different types of games and gameplay, memory modification cheats will cause different degrees of harm, such as: modifying the attack power of the characters in the game, modifying the number of unlimited gold coins, modifying the number of key props in the game, and so on, which will seriously jeopardize the fairness of the game and trigger the dissatisfaction of normal players.

Purchase props without consumption by modifying the selling price of commodities
Exe Emulator Modification
The exe emulator modification cheats is essentially a memory modification, but it runs on the PC as an exe program, while the game runs in the PC emulator. At this time, the cheats no longer reads and writes the memory of the game program, but reads and writes the data in the entire simulator, through repeated positioning, you can also achieve the effect of memory modification.There are two major difficulties in detecting this kind of cheats:
● No need to open Root permissions to search the memory for value tampering, making it difficult to detect by previous security environment detection programs.
● During the running of the game, the value will be changed in real time, so it takes a longer time to check the value, which seriously affects the efficiency of the confrontation.
Case Study of Speed Hacks
As we all know, the game needs to play the screen in frames, and to calculate the time needed to play each frame of animation, we need to call the C library function to get the system time. Such as:// Get the current precise time
gettimeofday;
// Get the system time.
clock_gettime;
This type of cheats works by modifying the system time to speed up or slow down the flow of time in the game. In addition, some of the speed hacks call UnityEngine_Time_set_timeScale and pass in the desired speedup multiplier to achieve the global speedup effect.
Due to the different gameplay, variable speed hacks can cause different effects, such as music and parkour games can slow down the speed to significantly reduce the game difficulty. While games involving formation can accelerate the progress of material collection and shorten the formation cycle of the game.

Reduce game difficulty by slowing down
This kind of cheats will seriously undermine the fairness of the game and cause dissatisfaction among normal players, and will drastically shorten the life cycle of the game if they are not stopped.
Code Tampering Case Study
Some cheats authors also use static analysis combined with dynamic debugging to directly modify the game client code logic by means of reverse analysis to create a “hacked version”. Commonly, the hacked version of the game will have an external function menu to realize the control of numerical modification, removal of advertisements and even internal purchase hack.
hacked version of a game comes with a cheat function.
This kind of hacked version of the game will come with a series of cheats functions to attract players, and its existence will seriously squeeze the space of the legitimate version, which will have a direct impact on the revenue of the game.
Case Study of Game Resource Tampering
Nowadays, there are various angles of game cheating. In addition to common cheating methods, the author of the cheats will also cheat through a variety of tricky angles, such as tampering with in-game resource files.For example, in the FPS game, the cheats authors tampered with the material of the map resources in the game, and modified it to be transparent, so as to realize the cheats function of “see-through”.

Compared with other cheats, the angle of this kind of resource tampering cheats is more tricky and difficult to detect, and once this kind of cheats appears, it will spread in a short time, causing very serious game balance problems.
Auto-Click Cheats Case Study
The common auto-click cheats can create automated simulated clicking scripts by setting parameters such as key positions, key sequences, and key intervals.
auto click function of a software
In a specific game environment, you can choose the auto-click program to realize the functions of automatic monster fighting, automatic quests, automatic keeping online and rewards. This kind of auto-click cheats will greatly affect the game balance and destroy the normal player's game experience.
Packet Intercept Cheat Case Study
In the process of game operation, when we click a button or perform a certain game behavior, the client will follow the rules agreed with the server to send the game behavior request and parameters to the server through the network packet, the server receives the request to make the analysis, the information will be processed and fed back to the client, and then the client will analyze the feedback information and display it to the players.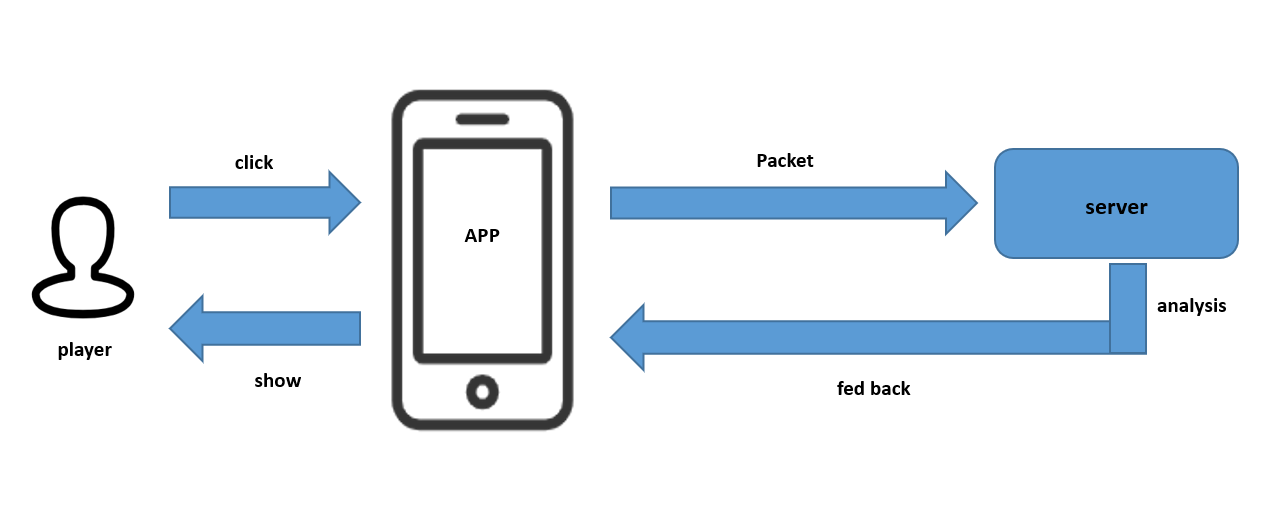
Normal state game data interaction
Hackers usually use packet grabbing tools to get game packet data. When the hacker captures the packet data and hacks it, he can tamper with the data up and down in the game, such as the attack power of the game character, the life value, the logic of winning and losing in the game, and the logic of surrendering and judging the loss, etc., so as to realize a series of cheat functions.
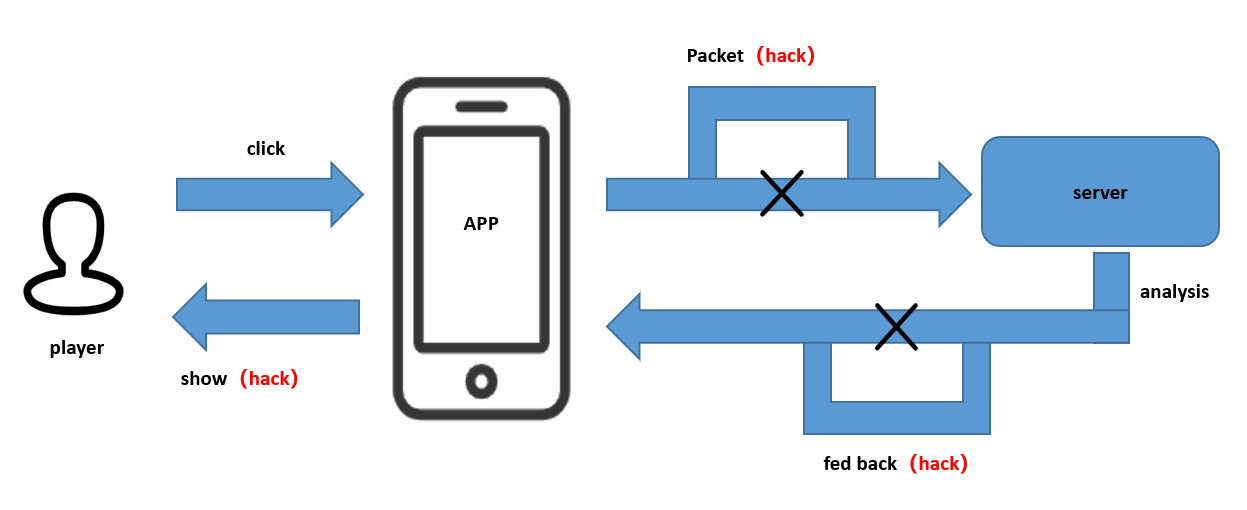
Client-server interaction after communication protocol hacking
Virtual Environment Case
The so-called virtual environment refers to the environment that is independent of or destroys the original system of the device, such as: iOS Jailbreak, Android Root, virtual machine, virtual framework, cloud cell phone and so on. This kind of virtual environment can provide a higher level of device permissions for cheats, which is a breeding ground for game cheats.How do games deal with the problem of cheats?
In the face of the increasingly large game black and gray industry infestation, game manufacturers are in urgent need of a strong, professional game security team, JikGuard technology-driven, research and development of a number of industry-exclusive technology, built for different scenarios and game types of the function of the matrix, can cover the whole game scene security issues.Anti-Cheat Features
JikGuard has developed a behavioral detection solution for games that face a series of risks from cheats modifications. With a 200+ dimensional intelligent sensing system, JikGuard can kill all kinds of cheats and their variants to provide effective protection.Anti-Hack Features
JikGuard's industry-exclusive “No API Signature Verification Technology” encrypts the game's engine and code in depth, and performs multiple checks on the signature of the game package and the integrity of the file, greatly reducing the likelihood of being bypassed, and preventing the game from being implanted with malicious modules, excluding advertisements and other behaviors.Active Recognition of Malicious Module Mechanism
Unlike other security products on the market, which need to obtain samples to fight against cheats, JikGuard's exclusive “active identification of malicious module mechanism” can actively identify suspicious modules in the game, and with the online combat function to achieve proactive defense, significantly shortening the cheats detection cycle.Anti-Injection Features
Prohibit the use of Xposed, Frida and other cheats module injectors to prevent malicious behavior such as modifying the game's memory after injection, and immediately flashback once discovered.Anti-SpeedHack Features
Adopting more underlying detection means and tested by a large number of real machines, and will immediately flashback the game once it detects a speedhack situation.Resource Encryption
JikGuard's exclusive resource encryption program, which penetrates deep into the game engine's bottom layer, combines the structure of the game's resource files and the loading mechanism to carefully construct the program.It provides high-intensity encryption protection for games with high compatibility, low consumption and no impact on performance. It supports Android/iOS/PC platforms and online resource updates. In addition, the solution has been specially optimized, without the need for development docking and access, encryption and decryption transparent to the development.